Orcus RAT 1.9.1 with 13 Plugins Cracked
Orcus RAT 1.9.1 + 13 Plugins Cracked
Remote Access Trojans (RATs) have become a significant concern in cybersecurity, enabling attackers to gain unauthorized access to and control over target systems. Among these, Orcus RAT has gained notoriety for its powerful features and widespread use in malicious activities. The cracked version of Orcus RAT 1.9.1, along with 13 additional plugins, represents an even more potent threat, as it offers extensive capabilities to attackers while being easily accessible to those with malicious intent.
Understanding Orcus RAT
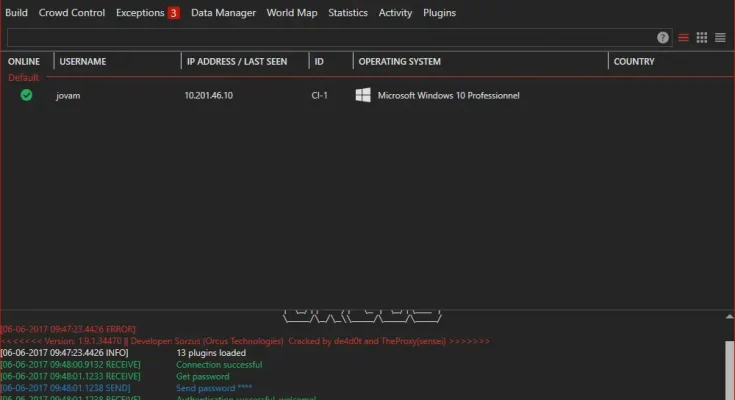
Orcus RAT was initially presented as a legitimate remote administration tool, designed to allow users to control their systems remotely. However, its features made it a favorite among cybercriminals, who began to use it for nefarious purposes. Orcus RAT allows an attacker to take full control of an infected system, including executing commands, capturing screenshots, logging keystrokes, stealing files, and even remotely accessing webcams and microphones.
The RAT is designed with a modular architecture, allowing users to extend its functionality through various plugins. This flexibility is one of the key reasons for its popularity among malicious actors. The plugins can perform a wide range of tasks, from network scanning and privilege escalation to data exfiltration and ransomware deployment.
The Threat of Cracked Versions
The cracked version of Orcus RAT 1.9.1 with 13 plugins represents an even more significant threat to cybersecurity. Cracked versions of software are modified to bypass licensing and payment requirements, making them available for free. However, these versions often come with additional risks, such as hidden malware or backdoors, which can further compromise the security of the attacker’s system or the systems they target.
In the case of Orcus RAT, the availability of a cracked version lowers the barrier to entry for cybercriminals. This means that even individuals with limited technical skills can access a powerful tool for malicious activities. The 13 included plugins enhance the RAT’s capabilities, making it an even more versatile tool for attackers. These plugins could include tools for keylogging, file management, system manipulation, and network reconnaissance, among others.
Impact on Cybersecurity
The proliferation of cracked RATs like Orcus poses a significant challenge to cybersecurity. Traditional defenses, such as antivirus software and firewalls, may not always detect these tools, especially when they are modified to evade detection. Moreover, the widespread availability of such tools increases the likelihood of attacks, as more individuals can access them.
The impact of an Orcus RAT attack can be severe, leading to data breaches, identity theft, financial loss, and damage to reputation. Organizations and individuals alike are at risk, as the RAT can be used to infiltrate systems, steal sensitive information, and even deploy additional malware.
Mitigation and Defense
Defending against threats like Orcus RAT requires a multi-layered approach. Organizations should ensure that their systems are up to date with the latest security patches and that they are using robust antivirus software capable of detecting RATs. Additionally, educating users about the dangers of downloading cracked software and the importance of practicing good cybersecurity hygiene is crucial.
Network monitoring and anomaly detection can also play a significant role in identifying and responding to RAT infections. By closely monitoring network traffic and system behavior, organizations can detect unusual activity that may indicate the presence of a RAT. Incident response plans should be in place to quickly contain and eradicate any detected threats.
Download
Choose a convenient way for you to download and download the file.
If the archive asks for a password, enter – enesoftware
| Mirrored | Download |
| Mega | Download |
| Ya.Disk | Download |
| Torrent File | |
| Download by magnet-link | |
| Loclouds | Download |
| Alternative link for bypassing blockades | Download |
To download files via Torrent File or magnet-link you need to download a torrent client. I recommend using utorrent
You can download the installer from our partners.