HiveRat Cracked 2024
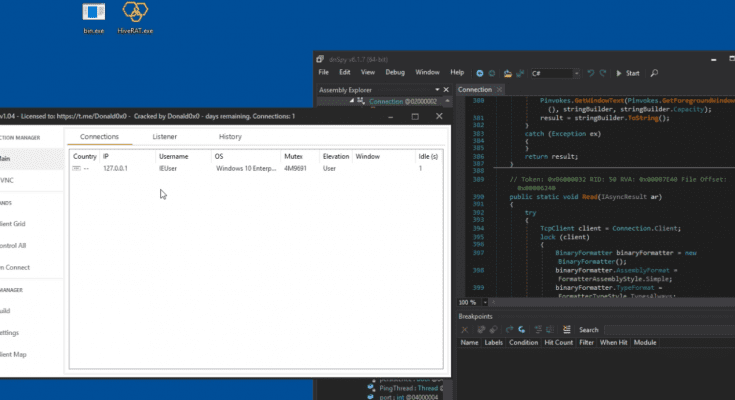
HiveRat is a sophisticated malware known for its stealthy infiltration and wide-ranging capabilities, posing a significant threat to cybersecurity worldwide. Operating as a remote access trojan (RAT), HiveRat can surreptitiously compromise systems, granting attackers remote control over infected devices without the user’s knowledge. This insidious malware is adept at evading detection by security software, making it challenging to eradicate once deployed. HiveRat’s arsenal includes keylogging, screen capturing, file manipulation, and data exfiltration functionalities, enabling cybercriminals to harvest sensitive information, spy on victims, and perpetrate various cybercrimes with impunity. Its modular design allows for customization, making it adaptable to diverse attack scenarios. Combating HiveRat requires a multi-layered approach, including robust cybersecurity measures, regular software updates, and user education to mitigate the risk of infection and minimize its damaging impact on individuals and organizations alike.
Feautres of Hive Rat Cracked 2023 :
HVNC:
– Fully Custom Build-IN Stable HVNC
– Completely Hidden Desktop Environment
– Windows 8-10+ Support
– Build in Hidden Browser Features
– Keyboard And Mouse Contror
HIDDEN BROWSER:
– Chrome Support
– Hidden Profile/Data Takeover
– Firewall Information
– Windows 7 Support
HiveRat Cracked 2023
REMOTE DESKTOP:
– Keyboard And Mouse Controll
– Multi Display Support
– Interval Quality Options
– Update & Upload / Exicute
– Open Web URL
REMOTE WEBCAM:
– Select Webcam
– Size/Quality
ON-CONNECT:
– Start hVNC
– Auto Save Client Passwords
– Run Custom Script
CONTROL ALL:
– Update Miner Settings
– Update All Clients
– Run Custom Script
– Start hVNC
– Auto Save Client Passwords
– Run Custom Script
USER DATA:
– Get GEO Location
– Grab Server Information
– Firewall Information
DATA RECOVERY:
– 35+ Browser Passwords
– FTP Client Recovery
– Get Discord Tokens
– Advanced File Manager
DATA CAPTURE:
– Advanced Keylogging
– Logs Over Email
– Email Screenshots
– Email Password Recovery
– Email Keylogger Keywords
– Save Logs To Disk
– Clipboard Logs
– Keylogger Keywords
– Live Keylogging
MINER:
– Mine BTC/LTC on target machine.
– Full proxy configuration for miner.
– Opton To Choose GPU:CPU:SILENT
BUILDER:
– .Net 4.0 / .Net 2.0
– Adcanced File Binding
– Icon Selection
– Assembly Cloner
– Advanced Assembly
– Hide/Melt File
– Extenstion Spoofer
– Execution Deley
– Custom Source Execution
– Password Protection
– Ganarate Mutex
– Delete ZoneID
PERSISTENCE:
– Persistence
– Process Protection
– Process Persistence
– Startup Persistence
– Startup
– Hidden Startup
– UAC Bypass
– Disable Taskbar
– Show/Hide Taskbar
– Show/Hide Tray
– Hide all Windows
– AntiVM/AntiSandbox
– Advanced Startup
– Kill Antivirus
– Disable RegEdit
MISC:
– Process Manager
– Remote Shell
– Registry Manager
– Listen On Startup
– Connect Notifications
– Server Actions
– Fun Options
– Gzip Compression
– Play Frequency
– Client Map
– Print Text
– Software Settings
– Client Grid
– History
If the archive asks for a password, enter – enesoftware
Download
Choose a convenient way for you to download and download the file.
If the archive asks for a password, enter – enesoftware
| Mirrored | Download |
| Mega | Download |
| Ya.Disk | Download |
| Torrent File | |
| Download by magnet-link | |
| Loclouds | Download |
| Alternative link for bypassing blockades | Download |
To download files via Torrent File or magnet-link you need to download a torrent client. I recommend using utorrent
You can download the installer from our partners.